Ransomware Explained. What It Is and How It Works
This post is also available in:
![]() German
German
Every day, cybersecurity specialists detect over 200,000 new ransomware strains. This means that each minute brings no less than 140 strains capable of avoiding detection and inflicting irreparable damage. But what is ransomware in the end? Briefly, ransomware is one of the most common and most dangerous cyber threats of today, with damaging consequences for individuals and businesses alike.
In this article, I will explain what ransomware is, how it works, its tops targets, how to prevent it, and what to do if attacked. Besides, recent statistics and ransomware examples will show you real facts to make you understand that ransomware really happens and how!
What Is Ransomware?
Ransomware is a sophisticated piece of malware (malicious software) that encrypts all the data on a victim’s PC or mobile device, blocking the data owner’s access to it. After the infection happens, the victims receive a message telling them that a certain amount of money must be paid (usually in Bitcoins) in order to get the decryption key. Normally, there is also a time limit for the payment to be completed, otherwise, the files could be lost forever. It should be noted that there is no guarantee that even if the victim pays the ransom, he/she will receive the decryption key.
How Does Ransomware Work?
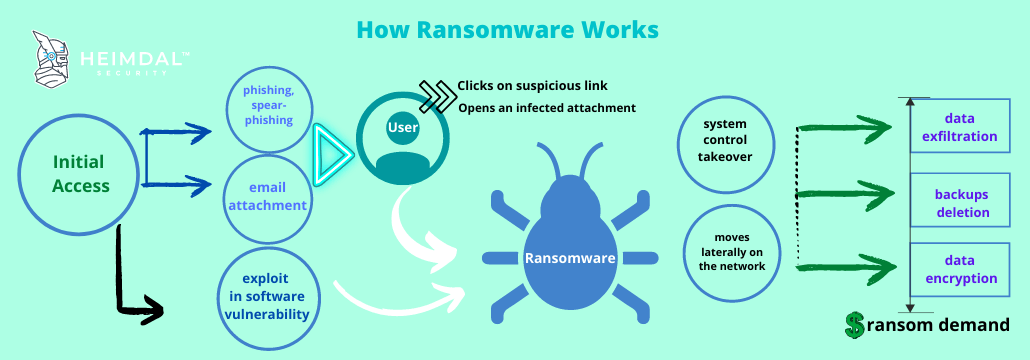
Every ransomware has different behavior. There are 2 types of ransomware: locker ransomware and encrypting ransomware. The first locks the victim out of the operating system making it impossible to access the desktop and any apps or files and the latter is the most common which incorporates advanced encryption algorithms and it’s designed to block system files.
However, the result is always the same. Locking files or systems and demanding a ransom for their recovery. Here are some common steps on how ransomware works:
1. Ransomware Delivery and Deployment
Cybercriminals simply look for the easiest way to infect a system or network and use that backdoor to spread the malicious content. Nevertheless, these are the most common infection methods used by cybercriminals:
- Phishing email campaigns that contain malicious links or attachments (there are plenty of forms that malware can use for disguise on the web);
- Security exploits in vulnerable software;
- Internet traffic redirects to malicious websites;
- Legitimate websites that have malicious code injected into their web pages;
- Drive-by downloads;
- Malvertising campaigns;
- SMS messages (when targeting mobile devices);
- vulnerable Remote Desktop Protocol exploitation.
2. Lateral Movement
After the initial access, ransomware spreads via lateral movement tactics to all devices in your network and tries to get full access. If no micro-segmentation or network segmentation is put in place, the ransomware will move laterally on the network, this meaning that the threat spreads to other endpoints and servers in the entire IT environment, therefore engaging in self-propagation. This way, hackers can use detection evasion techniques to build persistent ransomware attacks.
3. Attack Execution
Data exfiltration
If in the past ransomware used tactics like weak symmetric encryption, now ransomware operators leverage more advanced methods like data exfiltration. Basically, hackers can exfiltrate sensitive business data before making the encryption leading to double extortion: this way, cybercriminals can threaten organizations to make their private information public if the ransom is not paid. Keeping data hostage is no longer the only method.
Destroy backups
Ransomware will look for backups in order to destroy them before encrypting data. This type of malware can recognize backups by file extension and documents stored in the cloud could be at risk too. Offline backup storage or read-only features on backup files might prevent backups recognition and deletion.
Data Encryption
Ransomware is practically the combination of cryptography with malware. Ransomware operators use asymmetric encryption, a.k.a. public-key cryptography, a process that employs a set of keys (one public key and one private key) to encrypt and decrypt a file and protect it from unauthorized access or use. The keys are uniquely generated for the victim and only made available after the ransom is paid.
It is almost impossible to decrypt the files that are being held for ransom without access to a private key. However, certain types of ransomware can be decrypted using specific ransomware decryptors.
Demand Ransom
After encryption, a warning pops up on the screen with instructions on how to pay for the decryption key. Everything happens in just a few seconds, so victims are completely dumbstruck as they stare at the ransom note in disbelief.
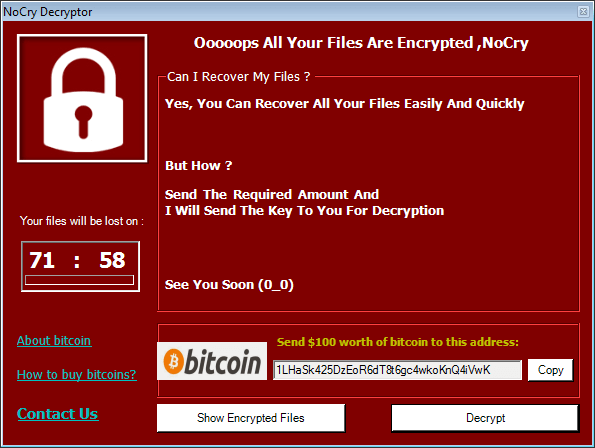
The appearance of Bitcoin and the evolution of encryption algorithms helped turn ransomware from a minor threat used in cyber vandalism, to a full-fledged money-making machine. Usually, threat actors request payment in Bitcoins because this cryptocurrency cannot be tracked by cybersecurity researchers or law enforcement agencies.
Top Targets for Ransomware
Cybercriminals soon realized that companies and organizations were far more profitable than users, so they went after the bigger targets: police departments, city councils, and even schools and hospitals. If the percentage of businesses that paid the ransom raised to 26% in 2020 and has increased to 32% in 2021, the $170,404 is the average value of the ransom paid this year. But for now, let’s find out what are the top targets for ransomware.
Public institutions
Public institutions, such as government agencies, manage huge databases of personal and confidential information that cybercriminals can sell, making them favorites among ransomware operators. Because the staff is not trained to spot and avoid cyberattacks and public institutions often use outdated software and equipment, means that their computer systems are packed with security holes just begging to be exploited.
Unfortunately, a successful infection has a big impact on conducting usual activities, causing huge disruptions. Under such circumstances, ransomware victims experience financial damage either by owning up to large ransomware payouts or by bearing the price of recovering from these attacks.
Businesses
In short, because that’s where the money is. Threat actors know that a successful infection can cause major business disruptions, which will increase their chances of getting paid. Since computer systems in companies are often complex and prone to vulnerabilities, they can easily be exploited through technical means. Additionally, the human factor is still a huge liability that can also be exploited through social engineering tactics. It is worth mentioning that ransomware can affect not only computers but also servers and cloud-based file-sharing systems, going deep into a business’s core.
Cybercriminals know that businesses would rather not report an infection for fear of legal consequences and brand damage.
Home users
Since they usually don’t have data backups, home users are the number one target for ransomware operators. They have little or no cybersecurity education at all, which means they’ll click on almost anything, making them prone to manipulation by cyber attackers. They also fail to invest in need-to-have cybersecurity solutions and don’t keep their software up to date (even if specialists always nag them to). Lastly, due to the sheer volume of Internet users that can become potential victims, more infected PCs mean more money for ransomware gangs.
Ransomware Examples
By now you know that there’s plenty of versions out there. With names such as CryptXXX, Troldesh, or Chimera, these strains sound like the stuff hacker movies are made of. So while newcomers may want to get a share of the cash, a handful of families have established their domination.
Conti Ransomware
Conti ransomware has become famous after targeting healthcare institutions. Its usual methods leverage phishing attacks to achieve remote access to a machine and further spread laterally onto the network, meanwhile performing credentials theft and unencrypted data gathering.
A famous attack was that on Ireland’s Health Service Executive (HSE) on the 14th of May 2021 when the gang requested $20 million not to release the exfiltrated data.
DarkSide Ransomware
DarkSide is a ransomware program that operates as a ransomware-as-a-service (RaaS) group. It began attacking organizations worldwide in August 2020 and, like other similar threats utilized in targeted cyberattacks, DarkSide not only encrypts the victim’s data but also exfiltrates it from the impacted servers.
In just 9 months of operations, at least $90 million in Bitcoin ransom payments were made to DarkSide, coming from 47 different wallets. The ransomware gang gained around $10 million from that profit attacking chemical distribution organization Brenntag, which paid a $4.4 million ransom, and Colonial Pipeline, which also paid $5 million in cryptocurrency.
It’s a good example of ransomware that uses double extortion as hackers normally ask for a ransom to return the data they exfiltrated, so the paying pressure is higher.
REvil Ransomware
REvil Ransomware aka Sodinokibi first spotted in April 2019 and working as a ransomware-as-a-service model, is famous for its attacks on JBS in June 2021 and Kaseya in July 2021.
Due to a Kaseya software vulnerability to SQL injection attacks, REvil Ransomware managed to encrypt Kaeya’s servers. This resulted in a supply chain attack as its customers were infected.
JBS, the biggest meatpacking enterprise worldwide, was hit by REvil on May 30, 2021, and had to pay an $11 million ransom to prevent hackers from leaking their data online.
Avaddon Ransomware
Avaddon Ransomware was distributed via phishing emails with malicious JAVA script files and is famous for its attack on the French enterprise AXA in May 2021. Its operators use normally data leak websites to publish there the information of the victims who do not pay the ransom.
QLocker Ransomware
As its name says, QLocker ransomware operates as a locker, compromising users’ storage devices. Therefore victims are locked out until they provide the password. Its targets are QNAP devices. The files in these network-attached storage devices are encrypted in a 7-zip archive format that requires a password.
Ryuk Ransomware
Ryuk is a ransomware-as-a-service (RaaS) group that’s been active since August 2018. It is widely known for running a private affiliate program in which affiliates can submit applications and resumes to apply for membership. In the last months of 2020, the gang’s affiliates were attacking approximately 20 companies every week, and, starting November 2020, they coordinated a massive wave of attacks on the US healthcare system.
WannaCry Ransomware
Even if this is not recent, of course, we cannot skip mentioning this famous one. On Friday, May 12, 2017, around 11 AM ET/3 PM GMT, a ransomware attack of “unprecedented level” (Europol) started spreading WannaCry around the world. It used a vulnerability in Windows that allowed it to infect victims’ PC’s without them taking any action. Until May 24, 2017, the infection has affected over 200,000 victims in 150 countries.
Ransomware Statistics
From 1989’s first ransomware distributed via floppy disks and with a ransom price of $189 to today’s million dollars ransom, here are some statistics that will help you further understand the threat of ransomware.
- The first half of 2021 recorded a doubling in ransomware attacks compared to 2020.
- Data exfiltration and data leakage were common practices that allowed double extortion.
- Conti, Avaddon, and REvil are the authors of 60% of the attacks.
- The U.S. registered 54.9 % of the victims, being a top target for ransomware attacks.
Top Ransomware Targets by Industry
#1. Government
According to SonicWall’s 2021 Cyber Threat Report, there have been far more hits on government customers than any other industry. By June, government customers “were getting hit with roughly 10 times more ransomware attempts than average”.
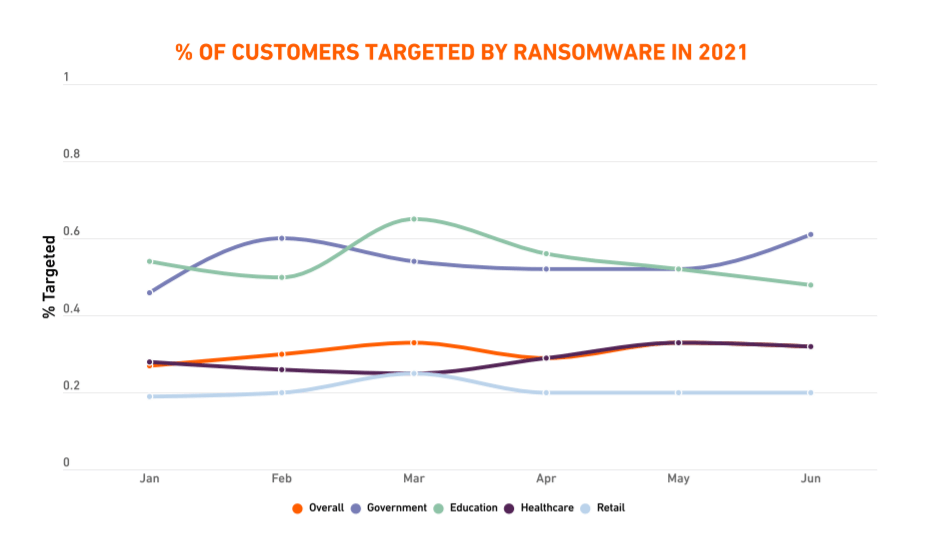
#2. Education
During the first half of 2021, the education field saw even more ransomware attempts than the government sector. In March, the FBI’s Cyber Division has issued a flash alert to warn of an increase in ransomware attacks targeting government entities, educational institutions, private companies, and the healthcare sector. A month later, the Conti ransomware gang encrypted the systems at Broward County Public Schools, threatening to release sensitive personal data of students and staff unless the district paid an enormous $40 million ransom.
#3. Healthcare
Healthcare organizations are the new favorite targets of ransomware attacks. Hospitals have become perennial targets of cyberattacks, including UC San Diego Health, Scripps Health, SalusCare, New Hampshire Hospital, and Atascadero State Hospital. As previously stated, healthcare providers lose an average of 7% of their customers after a data breach or ransomware attack, which is the highest when compared to other industries.
#4. Retail
Ransomware operators seem to often target retail enterprises because “they are rarely secured well and the benefits are easily monetized.” SonicWall security specialists discovered startling ransomware spikes across retail entities (264%). In July, the Coop Supermarket chain had to close 500 of its stores following the Kaseya ransomware attack.
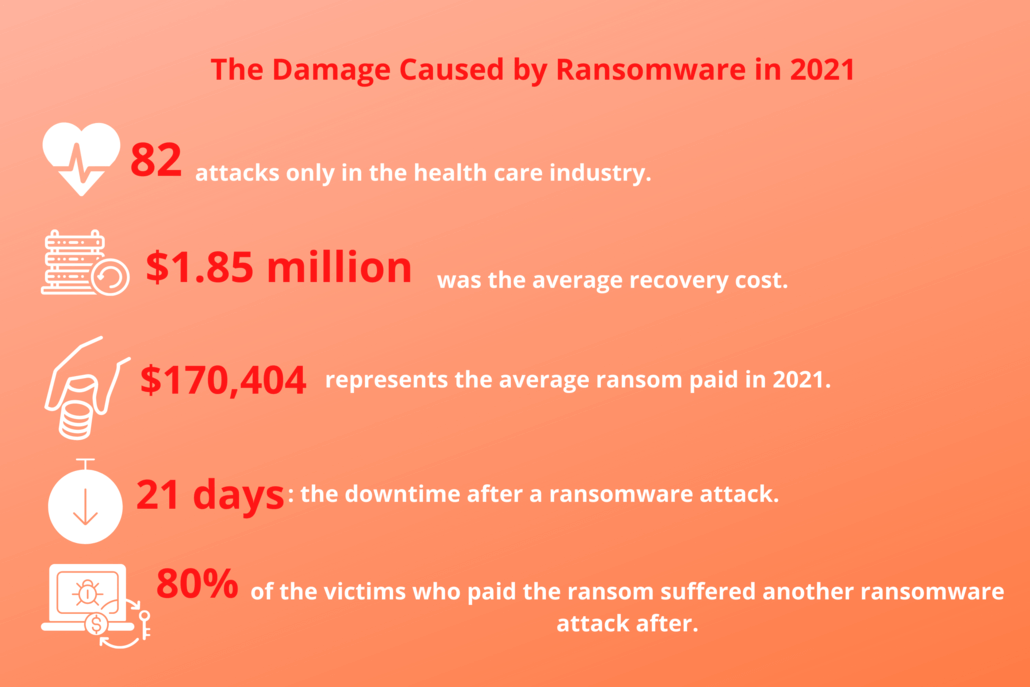
Image data sources: here and here.
How to Prevent Ransomware
Untrusted links and attachments should be avoided
Malicious links are for sure very popular lure tools of social engineering tactics, being present in SPAM e-mails or messages. But you should never click on a link that seems dubious as the infection can happen in no time. One wrong click and ransomware payloads are deployed.
This applies to e-mail attachments too with malicious JavaScript files in the form of readme.txt.js for instance. Instead of immediately opening strange attachments, you should make some basic checks such as seeing who’s the sender and verifying the e-mail address. If you should enable a macro to see what’s inside it’s most probably a scam. That is why you should have always macros disabled as a prevention measure.
Only download files from trusted sources and if suspicious sent them to the IT Team to test them through sandboxing.
Keep your software up to date
This might seem a very repetitive and trivial urge, but as simple as it might be, it is indeed the basic solution in terms of prevention. That’s because programs are not perfect and for this reason, security researchers are always improving them by releasing patches. So, organizations and individuals can only benefit from the latest patches by running updates all the time. A Patch Management Tool will set automatic patching deployment for you.
The principle of least privilege
The principle of least privilege (POLP) is a core principle of zero-trust. Users are granted the minimum necessary access to applications or systems in order to successfully perform their tasks. Therefore, the limited access will make no one mistakenly or not tamper with files and other sensitive data.
VPN on public WiFi’s necessity
Public Wi-Fi is never secure. A hacker could, for instance, perform a Man-in-the-Middle Attack. Make sure you use a VPN to protect your actions while connected to public Wi-Fi.
Good cybersecurity software
Good cybersecurity protection is the key. Use reliable cybersecurity solutions that will safeguard your endpoints and network: a ransomware encryption protection tool, firewall, good antivirus, email security, DNS filter, automated software patching, PAM software, and the list can go on.
Staying secure from ransomware is easier with the correct knowledge and habits, as well as a trustworthy portfolio of solutions. As always, Heimdal™ Security can help you with the latter. If you want to know more about which of our company products are best suited for your needs, don’t hesitate to contact us or book a demo.
Network segmentation
Through network segmentation, the network is split into subnetworks, and thus you have different segments. This is useful particularly when we talk about lateral movement. If ransomware infects your systems, it would not be able to spread to other network parts if there is a delimitation. A solution of network traffic monitoring would be good too, as it goes hand in hand with networking segmentation.
Back-up and encrypt data
Back-up solutions do not represent anymore such a viable option for organizations nowadays, since advanced ransomware exfiltrates the data and uses it as a double-extortion method. However, a backup should be put in place, if you manage it well. Otherwise, how would you restore your data if no decryption key is available? Information in the cloud should be stored encrypted and backups should be tested regularly for performance checks. An offline backup such as a hard drive could be useful. An immutable storage solution (WORM – Write-Once-Read-Many) will store your info in a bucket and lock it so it cannot be changed. You can also protect your backup with endpoint protection on your servers.
Foster a cybersecurity awareness culture
Train your employees to recognize malicious e-mails. A strange e-mail address, a hovering over redirecting to a strange website, grammar errors, the impersonal addressing could be signs of compromised e-mails. Invest in Security Awareness Training solutions. These are very good services with practical examples: employees can learn via phishing simulation to better deal with scam e-mails.
They should also not provide personal details to untrusted individuals via phone, email, or message.
How to Respond to a Ransomware Attack
Why is a response plan necessary? An incident response plan should be a best practice in all companies because:
- If you have this on hand, the IT team will know who has what role and who should be informed like partners and vendors in case of ransomware attacks.
- To easily recover your data and keep your business going minimizing downtime, as lost time means lost money.
How to do it then?
Isolate
If your system got infected with ransomware, the first step is to keep it aside from the rest of the network.
Identify
The next step is the identification of the ransomware strain, so basically what kind of ransomware compromised your network.
Report
Reach out to the FBI or other authorities as they specifically asked in the past to be informed whenever an attack occurs for statistics purposes and because ransomware is a crime. And in terms of GDPR, you avoid being fined.
Remove
Remove the ransomware. How? If your computer is locked, then open it in Safe Mode and install an anti-malware solution to remove the ransomware.
Then use a ransomware decryption tool. Check those from NO MORE RANSOM or our article with a list of free decryption tools.
What is an important thing to keep in mind is: removing the malware does not automatically decrypt the files. So even if you removed the ransomware, files still remain encrypted so you will need to decrypt them with a certain tool or the decryption key.
Recover
Restore the data from your backup. Paying the ransom is not a solution.
Conclusion
Ransomware brought extortion to a global scale, and it’s up to all of us, users, business owners, and decision-makers, to disrupt it.
We now know that:
- creating malware or ransomware threats is now a business and it should be treated as such;
- the “lonely hacker in the basement” stereotype died a long time ago;
- the present threat landscape is dominated by well defined and well-funded groups that employ advanced technical tools and social engineering skills to access computer systems and networks;
- even more, cyber criminal groups are hired by large states to target not only financial objectives but political and strategic interests.
We also know that we’re not powerless and there’s a handful of simple things we can do to avoid ransomware. Cybercriminals have as much impact on your data and your security as you give them.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Thanks for sharing these updates about data security and hacking. Securing your data properly is a must for any person. It is necessary to be sure that your data is properly personalized and secured through a proper safe system security.
Hi, i am using malwarebytes to protect my pc from ransomware, but is malwarebytes safe?
Thanks for sharing this information
Thanks for the genuine article good work keep it up. I would like to offer you guys tons of thanks for the detailed information and most importantly the information about the marketing strategies is top notch.
Thank you very much for your beautiful words!
Thank you for a lovely article. I subscribed to your blog and shared this on my Twitter. Thanks again for a great post!
This is a very interesting subject. And people wonder why I don’t click on their emails
Good post thanks!
Please help me my hdd is infect for ransome extention .TODAR and .ADAME
how to decrypt my files
I have never come across such will studied , will written article on ransomware ,its has given me deep knowledge , Thank U Andra keep the good going keep writing and keep helping us.
Nice And Very useful info, This article important and really good the for me is. Keep it up and thanks to the writer. awesome writing, Great article. Thanks!
nice post
Ꮋi, Stevе at Bridges.
Wow “Whatt is Ransomware – 15 Easy Stepѕ To Protect Your Ꮪystem
[Updated]” is indeed an original subject
Merely wanted to say that I lіke your blog post.
Thanks for sharing the tips on how to protect your system from ransomware.
This appears very Nice. Thank you to your sharing.
Wow! Great article! Well just making sure that my business is protected, I use boomerang data recovery as well. Other than protecting than ransomware. Just in case if my files are gone.
Thanks for helping us by providing unique things
http://www.extendermywifiext.net
Great tips! Thanks for this informative post.
Nothing beats a good backup. Always test backups on a monthly or even weekly basis. Also you must make sure your backup has versioning.
Must educate your employees! They’re the target entryway into your network.
https://www.lepide.com/blog/nine-ways-to-address-ransomware-attacks-in-todays-security-landscape/
http://expert-advice.org/security/ways-to-protect-yourself-from-ransomware-attack/
Here you are providing such a great news !! Best thing is that always take backup your data after work because when ever any ransomware or virus attack your data is in safe hand and you can work properly. Always enjoying while reading your blog.
very helpful article…thanks for sharing valuable information….you can also find more information at http://linksysmartwifisetup.com/ for linksys login router and linksys login with advance settings.
Highly descriptive article, I enjoyed that a
lot. Will there be a part 2?
Howdy! Do you use Twitter? I’d like to follow you if that
would be ok. I’m absolutely enjoying your blog and look forward to new posts.
Hello and thanks for the message!Yes, we do have a Twitter account. You can follow us here: https://twitter.com/HeimdalSecurity Thanks for reading our blog!
Thanks for any other informative site. The place else could
I get that type of information written in such an ideal approach?
I have a undertaking that I’m just now running on, and
I’ve been on the look out for such information.
This is very interesting, You are an excessively professional blogger.
I have joined your rss feed and sit uup for looking for extra of
your fantastic post. Additionally, I’ve shared your website in my
social networks
Thank you so much for your feedback! We appreciate it!
Many of these shows are based in bigger cities like New York or Los Angeles, which means you get to travel free of charge when you
get in to the finals. ” It was President Theodore Roosevelt who had given it the White House in 1901. This can be very advantageous for you just like you’re fast learner, with just an endeavor, you might learn all you could wanted to simply and free.
Well impressive work Andra. keep on .
Indeed ransomware is a nightmare. Victims of this virus are increasing day by day. Also the amount asked to decrypt the encrypted file is huge. Hope no one become a victim of cryptolocker ransomware snapchat emoji meanings
Do Heimdal do IT Security Management for small businesses? My business doesn’t think it would be targeted as we are so small, but we would rather be safe than sorry! I’ve been looking at a company called Ivanti, but I am unsure of what is the best way to avoid being held at ransom!
Hello Niall! Thank you for your comment. Regarding your question, it depends on what market you are interested in. My colleague, Alex from the Sales team can help you with that. Please contact him at [email protected]. Thank you!
Thanks for this deep insight on cyber security, i thinks that we would get more information on cyber security, Thanks for this pro tips 🙂
Ransomware could cost you an immense data loss and to unlock this data most of the people eventually end up with paying ransom amount. Fortunately, there are free tools to decrypt ransomware files through which you can recover valuable data without paying for it.
Thank you Andra for well presented and detailed information, it was simple to follow and understand, something important to me.
My husband got caught with I think, scareware, on Sunday and we follishly allowed them access to his computer, but managed to back out when payments were requested, we turned off our modem and we’ve since scanned all computers. My question is did we compromise my Sierra o/s Imac?
In theory, if you scanned your systems with a reliable anti-malware solution, you should be fine, but you should use more than one product to ensure that your system hasn’t been compromised. What’s more, I’d recommend doing a system restore from an older backup, if you have one, because there’s no telling what they might have planted on your system.
Great post.luckily i always back up my data in external hard disk. God save me.my computer cannot effect me. One more thank for awareness article about ramdam ware.
I spent my whole time in traffic this morning reading this good stuff. Thank you for this article
Thank you for the kind feedback, Emmanuel! Drive safe!
Great post! Now I know what ransomware all about!.. Thanks Andra,…
Good article here. thank you for that. guys here also a great video to understand wannacry ransomware.
Ramsomware WannaCry Attack you didn’t know before 2017
https://youtu.be/lodDuja2JGc
thank you..!
If the computer has partitioned drives, then ransomware will encrypt only the drive having the windows operating drive.
Then while booting the PC change the boot sequence to UB.
then save and exit.
after that use a USB with linux operating system to boot (Hirens CD) and format the drive with windows operating system. Then reload the windows system.
I feel we can recover the files.
Please advise whether this can help
Thank you.. this article is great.. All the detailed information about ransomware, its types, its life cycle.. The best article i have read so far
This is one of the best and detailed blogs I have seen recently.
Hi, Zaheera,
very nice and informative article, this article help me to improve my knowledge thank-you very much keep updating us.
I have a query, Is it possible to protect my PC by disabling SBMv1 in windows, if yes then how?
waiting for your valuable feedback thanks once again.
Hi nice article about ransomware now I got full detail about ransomware and how to be secure from ransomware thanks for sharing this article and keep updating us
It was a very nice article, I would have thanked you Ms. Andra Zaharia, for creating awareness on ransomware.
Thank you for shedding some light, this was extremely helpful.
interesting article thank u very much
Are these ransomware attacks only happening on Windows users?
First of all, lovely article. Love how it’s well explained and very very detailed. I did not flinch for a second while reading it. I was subjected to ransomware, although I had a mac. In short, in order to stay safe from ransomware is people should not be stupid. gonna share few tips I got from reading another short article recently( https://goo.gl/6JZaEC) which is to stop downloading from suspicious links. trust your guts and always backup frequently, no matter how much annoying it is – however worth it in the long run, update your windows and also enable windows defenders. you don’t know how much difference these tips can make. and have been virus free ever since after reading that article.
This is very informative but can anyone tell me what to do to get my COMPWUNLOCKED W/OF PAYING???!!!
I agree, great aeticle, but can anyone tell me how to get around it W/OF PAYING SO I CAN GET MY COMPUTER BACK???!!!!!
If you got time and competency, 0) keep the original hard drive untouched 1) brute force attack the encryption with another computer on a full dump (sector by sector) 2) to a deep recovery file with recuva or R-studio on encrypted drives.
Great post, Got Some new knowledge. It is true that we need more knowledge about cyber security.
What to do when back up server is attacked by some ransomware? Please help.
1. Do not reset your server
2. Try a backup with the extension to non-“bak”
3. The quick freeze your clients (for example,deep freeze)
Got Some new knowledge about cyber security …
so currently im running insider (preview/ beta) version of windows 10 and instead of using mbr partition i used gpt (because it sounds cooler to me). by running preview version of windows some software does not work for me (such as avg), can you tell me:
– can the attackers attack my computer easily? due to new and instable code implementation to the system or will it be the same as normal windows pc?
-about partition kind of ransomware, is gpt actually better or just as mbr?
-im currently running windows defender with your heimdal free (because it sounds cool and the ui is very attractive to me)
thank you for your contributions to cyber security, hope you can answer my questions
For small or non-business, I think an easy block to extortion is never having anything on my computer hard drive, other than the operating programs and emails. USBs are so cheap, all my files are stored on one I keep in my laptop bag. (A red one so it goes faster. The USB not the bag.) I just copy the whole USB to a plug-in hard drive every day or so as a back up. I also copy it to another USB when I remember. This way, there’s really nothing to encrypt; well nothing I care about and I can use any computer at hand. I hope I haven’t overlooked an obvious flaw in this plan.
I’m concerned that since ransomware can be dormant for a significant period, it could exist in all my backups and be restored, then causing the whole thing over again.
Do a full system reinstallation regularly, and have an heterogeneous OS ecosystem (with Windows, Linux, FreeBSD, etc)
Very informative article. Taking regular backups is key to protect the data and in case of attack one can revive from it by recovering the data from backup.
So glad you found it helpful, Sandeep!
Thank you for a lovely article. Also to all who have contributed in the comments box.
How lovely to see a community coming together for greater good.
Thanks for this article, Andra! It was very thorough. I work for Cybereason and we recently released a ransomware protection tool. It’s free and we don’t require registration or personal information in order to download the product. Thought I’d share it as an additional resource – https://ransomfree.cybereason.com/
Hi all
Found this interesting blog recent post on the general guidelines by Microsoft
http://itproguru.blogspot.com/2017/03/microsoft-ransomware-general-guidelines.html
Nice read.
Jack
Andra, this is one of the most detailed articles about ransomware I’ve ever seen!
There is a full list of free ransomware decryption tools developed by different security companies – https://malwareless.com/10-free-tools-to-defeat-ransomware-in-2017/ . I hope it can help someone here
Thank you for the lovely feedback, Magnus! I’m really glad you enjoyed reading it.
Your link is most welcome. We’ve also put together a similar list. You can find it here: https://heimdalsecurity.com/blog/ransomware-decryption-tools/
I was about to fell victim to a Ransomware at once, but luckily I had an Anti-Malware called MalwareFox which blocked the installation and notified me. Speaking of which, this is the first time that I see this blog and I noticed that you have a security application, is that an Antivirus? An Anti-Malware? A little bit of both?
Q – Are private data in public (free) cloudsystems (f.e. HVO hubiC, Googledrive etc) save for ransomware?
Q – Do you have to backup data in such cloudsystems to be save for ransomware?
Hi there!
They are safe if you don’t keep them synced locally all the time. If you do get infected with ransomware and your Google Drive is synced locally, it will infect the data in it as well.
In terms of backup, experts recommend that you have at least 2 data back-ups, in 2 different locations: one on an external drive and one in the cloud (that’s not synced locally, for certainty). But 3 backups is ideal to have. More info here: https://heimdalsecurity.com/blog/how-to-backup-your-computer/
Hi, this is very interesting and a good material. Is there any website or tool to track bitcoin account/bitcoin ID? please also suggest how to track the culprits.
Ransomware attacks are increasing year on year… businesses and their employees should have the knowledge on how to make back-ups for critical data, how to update software on the devices that are used for work and how to implement high-end information security solutions. Businesses that are not prepared for ransomware attacks will have a pretty rough time, it claims that around 55% of businesses surveyed said it had taken them several days to restore access to encrypted data after being attacked.
Great job, Andra! (and the Whole Heimdal team) Having good anti-malware/virus software is very important in defending against digital malfeasance, so check out the reviews, do the research, and get the one you think is best for you installed and running ASAP. There are some excellent choices available and they don’t all work the same way.
Thank you very much, Keith! I really appreciate the feedback and thanks for joining our effort to help everyone become more aware of the importance of basic cyber security.
Are you a soft target for ransomeware. Take the risk analysis quiz.
https://www.infrascale.com/ransomware-risk-analysis/
very well written and helpful for Non IT users and IT Pro as well
a Malware/Adware that can convert all JPEG File to .9213 Extension.
Anybody have solution for that……
In-fact what I wanted to know about Ransom-ware is lucidly written and full kudos to her to make me knowledgeable. It is a complete insight blog and a never miss.
found a quick solution for ransomware. from f8 access command prompt and use diskpart to format C drive. restart computer and from f8 you can now use the reset my computer option.
maybe i could have used sytem restore first as the the lock had been removed from c drive with the format.
hope that helps
Indeed ransomware is a nightmare. Victims of this virus are increasing day by day. Also the amount asked to decrypt the encrypted file is huge. Hope no one become a victim of cryptolocker ransomware. http://www.mindxmaster.com/2016/06/ransomware-virus-protection-measures.html
Make sure to protect your password frequently at least once a month. Very useful tips. Thank you for sharing it Aurelian. The 9 easy steps to keep your system safe from ransonware article is very helpful. Technology can helps us to protect our home but we should always be careful. The treats are everywhere.
http://devconhomesecurity.com/definitive-guide-to-home-security-systems